LDAP configuration
In contrast to many other server configurations OpenLdap supports parameter configuration within its own database backend. In other words: Some parameters are not being stored in configuration files.
Actually OpenLdap still supports an alternate configuration file based approach which may be activated. Its use however is discouraged according to the documentation:
Note
The older style slapd.conf(5) file is still
supported, but its use is deprecated and support for it will be
withdrawn in a future OpenLDAP release.
The DIT style configuration may be altered
by LDAP clients like ldapmodify
using .ldif files. An alternate way requires
altering the server's configuration
/etc/ldap/slapd.d/cn\=config/olcDatabase\=\{0\}config.ldif.
We start by gathering required information. Note: The
ldapsearch command is part of the
openldap-utils package:
ldapsearch -Y EXTERNAL -H ldapi:/// -b cn=config
# {0}config, config
dn: olcDatabase={0}config,cn=config
objectClass: olcDatabaseConfig
olcDatabase: {0}config
olcAccess: {0}to * by dn.exact=gidNumber=0+uidNumber=0,cn=peercred,cn=external
,cn=auth manage by * break
olcRootDN: cn=admin,cn=config
# {1}mdb, config
dn: olcDatabase={1}mdb,cn=config
...
olcRootDN: cn=admin,dc=hdm-stuttgart,dc=de
olcRootPW: {SSHA}7M0gUyHOH7cfK1z9amqgK0uQcn84AuYw
...The above lines appear near in the tail section. We see two
databases {0} and {1} representing two
different DITs namely cn=config (the
configuration database) and dc=hdm-stuttgart,dc=de
(containing our “actual” directory data).
The configuration database does have a olcRootDN:
cn=admin,cn=config entry but a corresponding
olcRootPW attribute is yet missing. This limits
configuration access to localhost.
External access e.g. by Apache Directory Studio requires adding this credential attribute. This first-time (bootstrapping) configuration must be done locally by means of an LDIF file adding a (possibly different) hashed password:
root@sdi8a:~# cat ~/add_olcRootPW.ldif
dn: olcDatabase={0}config,cn=config
add: olcRootPW
olcRootPW: {ssha}pHE+EPOG2gyRyOgjvFqsWOb5zGsGl9CDActivating this configuration my be effected by using ldapmodify:
root@sdi8a:~# ldapmodify -Q -Y EXTERNAL -H ldapi:/// -f ~/add_olcRootPW.ldif
modifying entry "olcDatabase={0}config,cn=config"This activation in turn enables a new account:
- Bind DN:
-
cn=admin,cn=config - Bind password
-
***** - Base DN
-
cn=config
When configuring a connection to access this configuration database you may have to untick Apache Directory Studio's “Get base DNs from Root DSE” box in the “Browser Options” tab. Then configure "cn=config" in the “Base DN:” manually.
We may now dynamically alter ourserver configuration parameters remotely using e.g. Apache directory studio:
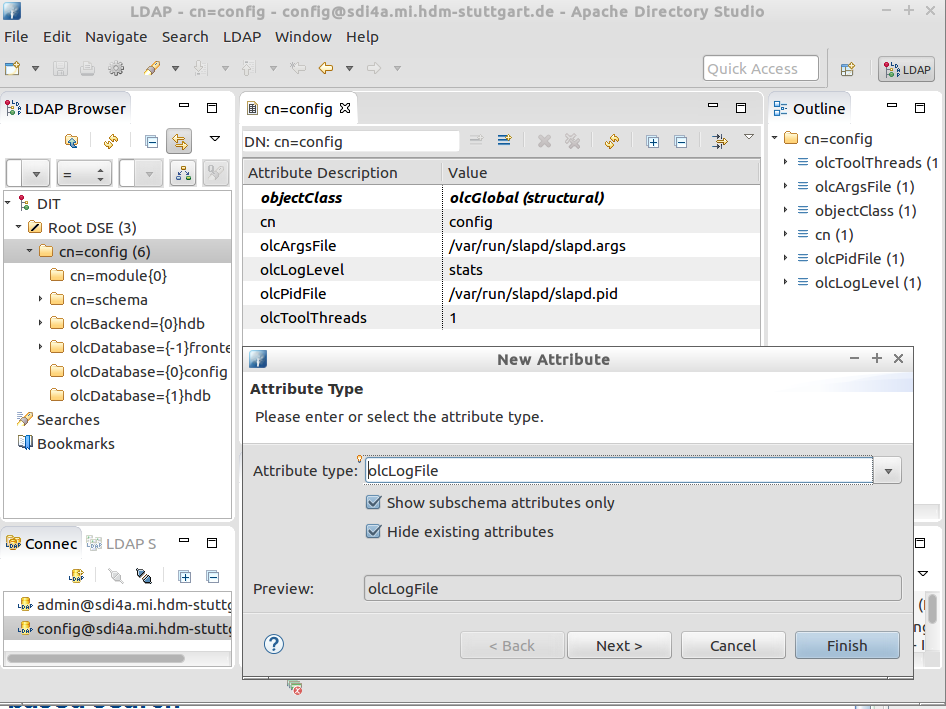
A prominent configuration change candidate is our server's log
level: Depending on your success during subsequent exercises you may
want to adjust olcLogLevel
in cn=config appropriately.
Caution
Using using
olcLogFile will not override OpenLdap using your host's syslog
facility: The file will be created (provided write permission is being
granted) but log messages will still be written to
/var/log/syslog.
Thus creating a separate ldap.log file
requires configuring
your system's syslog daemon appropriately. Current systems
allow for creating a file i.e.
/etc/rsyslog.d/slapd.conf containing the desired
log data redirection. Do not forget to restart your service.