Sanitizing user input
- Keep the database server from interpreting user input completely.
-
This is the preferred way eliminating security issues completely as being discussed in the section called “
java.sql.PreparedStatement”.May not be possible in legacy applications due to required efforts.
- Let the application check user input beforehand
-
Malicious user input is being rejected from being embedded into SQL statements.
Regular expression matching user names.
| Regular expression | User input |
|---|---|
[a-zA-Z]+ |
Matches
“Jennifer” |
Does not match “DROP TABLE
Users” |
So we have an “interceptor” sitting between user input fields and SQL generating code:

Using regular expressions in Java™
|
Q: |
This exercise is a preparation for Input validation by regular expressions . The aim is to deal with regular expressions and to use them in Java™. If you don't know yet about regular expressions / pattern matching you may want to read either of: Complete the implementation of the following skeleton: ...
import java.util.regex.Matcher;
import java.util.regex.Pattern;
public static void main(String[] args) {
final String [] wordList = new String [] {"Eric", "126653BBb", "_login","some text"};
final String [] regexpList = new String[] {"[A-K].*", "[^0-9]+.*", "_[a-z]+", ""};
for (final String word: wordList) {
for (final String regexp: regexpList) {
testMatch(word, regexp);
}
}
}
/**
* Matching a given word by a regular expression. A log message is being
* written to stdout.
*
* Hint: The implementation is based on the explanation being given in the
* introduction to {@link Pattern}
*
* @param word This string will be matched by the subsequent argument.
* @param regexp The regular expression tested to match the previous argument.
* @return true if regexp matches word, false otherwise.
*/
public static boolean testMatch(final String word, final String regexp) {
.../* to be implemented by **YOU** */
}As being noted in the Java™ above
you may want to read the documentation of class
The expression '[A-K].*' matches 'Eric' The expression '[^0-9]+.*' ... ... |
|
A: |
A possible implementation is given by: |

Input validation by regular expressions
|
Q: |
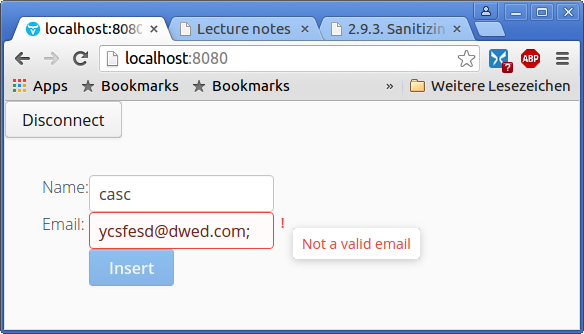
The application of Attack from the dark side proved to be vulnerable to SQL injection. Sanitize the two user input field's values to prevent such behaviour.
TipVaadin does provide regular expression based
validation support. You may want to consider |
|
A: |
Validation will be based on both on regular
expressions and Vaadins built in @Override
protected void init(final VaadinRequest vaadinRequest) {
...
// Sanitizing user names by regular expression
nameField.addValidator(new RegexpValidator("[^;\"'()]+",
"Sorry but this does not appear to be a user's name"));
// Adding an input validator for sanitizing username and e-mail input values.
// Caveat: Vaadin's validator will refuse e.g. "domainregistry@de"
// and may generally be non-RFC compliant.
emailField.addValidator(new EmailValidator("Not a valid email"));
...
}
...
void conditionallyActivateInsertButton() {
final boolean isValid =
0 < nameField.getValue().trim().length() &&
nameField.isValid() &&
// empty fields are not being validated!
0 < emailField.getValue().trim().length() &&
emailField.isValid();
... |