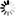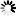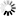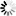Exercises are based on the OpenLDAP server
implementation.
Related material at http://www.openldap.org.
-
Lightweight Directory Access Protocol
-
Vendor independent
-
Clients interact with servers using a directory access protocol
| Command | Result |
|---|---|
ldapsearch \ -h localhost ❶ \ -D "cn=admin,dc=betrayer,dc=com" ❷\ -w password -x ❸\ -b "dc=betrayer,dc=com" ❹\ -s sub ❺ \ -LLL ❻ |
dn: dc=betrayer,dc=com ❶ objectClass: top objectClass: dcObject objectClass: organization o: Betrayers heaven ❷ dc: betrayer dn: cn=admin,dc=betrayer,dc=com ❸ objectClass: simpleSecurityObject objectClass: organizationalRole cn: admin ❹ description: LDAP administrator userPassword:: e1NT...dE53N1E= ❺ |
|
|
dn: uid=clark,ou=finance,dc=betrayer,dc=de ❶ cn: Sandy Clark homeDirectory: /home/clark sn: Clark uid: clark ❷ uidNumber: 21101 givenName: Sandy loginShell: /bin/bash mail: clark@betrayer.com ❸ mail: finance@betrayer.com postOfficeBox: 10G userPassword: {SSHA}noneOfYourBusiness
|
The entry's absolute distinguished name (DN). This name/value list uniquely identifies an entry (an its position) within a given DIT. |
|
|
This key/value combination is guaranteed to be unique within
respect to the given parent node. It allows to identify each node with
respect to its parent. So in a relational model the
“ In other words: There is only one such entry below ou=finance,dc=betrayer,dc=de having an uid attribute of value clark. |
|
|
LDAP allows for multi valued attributes. |
-
Structuring LDAP entry data.
-
Categories:
-
Structural
-
Auxiliary
-
Abstract
-
|
|
Class | Instance uid=clark,ou=finance,dc=betrayer,dc=de ----------------------------+--------------------------------------------------- inetOrgPerson (structural) | sn | sn: Clark cn | cn: Sandy Clark ... | ▲ | ┃ posixAccount (auxiliary) | ┃ cn | see above ❶ gidNumber | gidNumber: 23113 homeDirectory | homeDirectory: /home/clark uid | uid: clark uidNumber | uidNumber: 21101 userPassword | userPassword: {SSHA}noneOfYourBusiness .....
|
The cn attribute is being defined both in
object class |
RFC 4520 defines three LDAP search scopes:
-
baseObject (
base) -
singleLevel (
one) -
wholeSubtree (sub)
RFC 4520 defines predicate based queries using RPN style:
-
(| (cn=k*) (uidNumber < 2000))
-
Anonymous bind: No user credentials.
Note: This typically provides limited privileges.
-
Simple bind: User's DN + password:
DN: uid=clark,ou=finance,dc=betrayer,dc=de password: 123456789
dn: uid=clark,ou=finance,dc=betrayer,dc=de
objectClass: posixAccount
objectClass: inetOrgPerson
cn: Sandy Clark
homeDirectory: /home/clark
sn: Clark
uid: clark
uidNumber: 21101
givenName: Sandy
loginShell: /bin/bash
mail: clark@betrayer.com
mail: finance@betrayer.com
postOfficeBox: 10G
userPassword: {SSHA}noneOfYourBusiness-
An OpenLdap server may host multiple DITs each being represented by its own database backend.
-
The server's configuration is itself being stored as a separate tree.
-
Each tree refers to a separate database backend. Thus the above example featuring two trees is being implemented by two database instances.